Home » PSApedia
Information security audit results
Explore Your Information Security Audit Results. Comprehensive Insights and Robust Solutions.
What is an Information Security Audit?
An Information Security Audit is a systematic, measurable technical assessment of how an organization’s security policies are employed. It is a comprehensive review of the information systems, which ensures that the necessary safeguards are in place to protect data.
This includes evaluating procedures, networks, and systems, checking for vulnerabilities, and verifying that all assets are fully protected.
Importance of Information Security Audit
PSA platforms manage client information, financial data, and project details, making them prime targets for cyber threats. Audits identify vulnerabilities, assess compliance with security standards, and help mitigate risks, ultimately safeguarding the integrity of client information and the reputation of professional service providers. In today’s digital age, data breaches and cyber threats are becoming increasingly common. This makes it essential for businesses to ensure that their data is secure. An Information Security Audit:
1. Identifies Vulnerabilities: Before a hacker does.
2. Ensures Compliance: Many industries have regulations that require companies to safeguard their data. An audit ensures that a company is compliant, avoiding potential legal issues.
3. Builds Trust: Customers and partners will have more confidence in a business that takes security seriously.
4. Protects Assets: Ensures that a company’s digital assets are secure and not at risk.
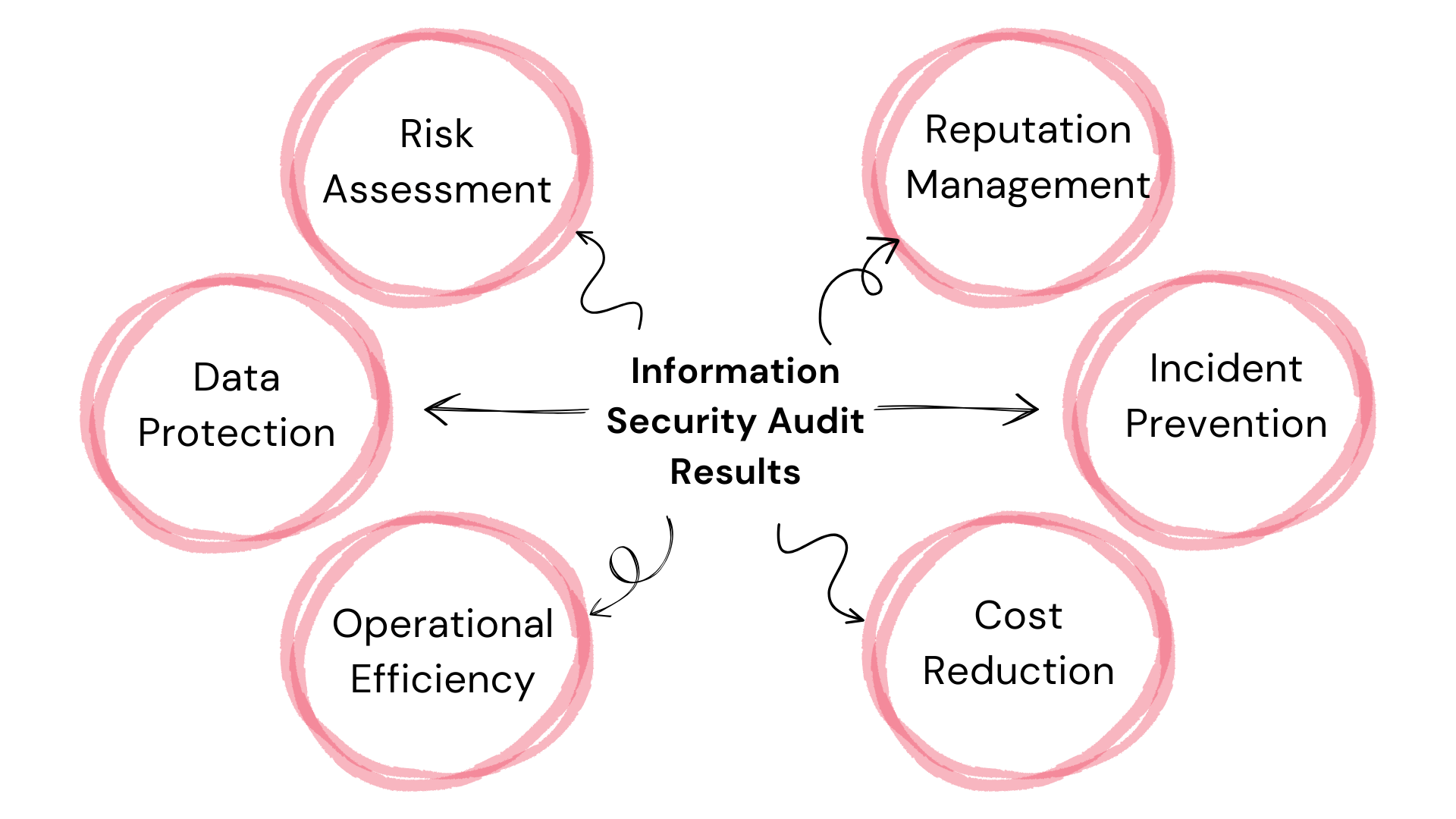
Importance of Information Security Audit
Calculating the Effectiveness of an Information Security Audit
Formula:
Effectiveness (%) = (Number of Issues Addressed / Total Number of Issues Identified) x 100
Example:
If an audit identifies 100 potential security issues and 90 of them are addressed, then:
Effectiveness = (90/100) x 100 = 90%
This means the audit was 90% effective.
Information Security Audit vs Other Security Assessments
While an Information Security Audit is comprehensive, there are other security assessments like vulnerability assessments and penetration testing. The main difference is:
1. Information Security Audit: Focuses on the strategies and processes in place, ensuring that they align with the company’s security policies.
2. Vulnerability Assessment: Identifies, quantifies, and prioritizes vulnerabilities in a system.
3. Penetration Testing: Simulates a cyber-attack to find vulnerabilities before a real threat does.
| Aspect | Information Security Audit | Other Security Assessments |
|---|---|---|
| Objective | Evaluate compliance with security standards and policies. | Identify vulnerabilities and risks in the security infrastructure. |
| Scope | Comprehensive review of the entire security program. | Focused on specific areas, systems, or processes. |
| Independence | Usually performed by an external auditor or third party. | May be conducted by internal teams or external specialists. |
| Reporting | Formal reports with compliance findings and recommendations. | Technical reports detailing vulnerabilities and mitigation steps. |
How Information Security Audit is Used?
An Information Security Audit is used to:
1. Establish a Baseline: Understand the current state of security.
2. Develop Strategies: Based on the findings, companies can develop strategies to address vulnerabilities.
3. Regular Monitoring: Regular audits ensure that the company remains compliant and that new threats are identified and addressed.
Ready to Optimize Your Information Security Audit?
KEBS, a leading Professional Service Automation (PSA) software, offers tools that can help streamline the audit process. With KEBS, reduce the time and effort required for an audit. Get instant insights into your security posture.
Understand your security landscape at a glance with a Comprehensive Dashboards. KEBS can be integrated with other business systems, ensuring that all data is secure.
Moreover, KEBS offers a range of solutions that can help businesses in various areas, from project management to finance and resource management. With KEBS, you can ensure that your business is not only secure but also efficient and competitive.
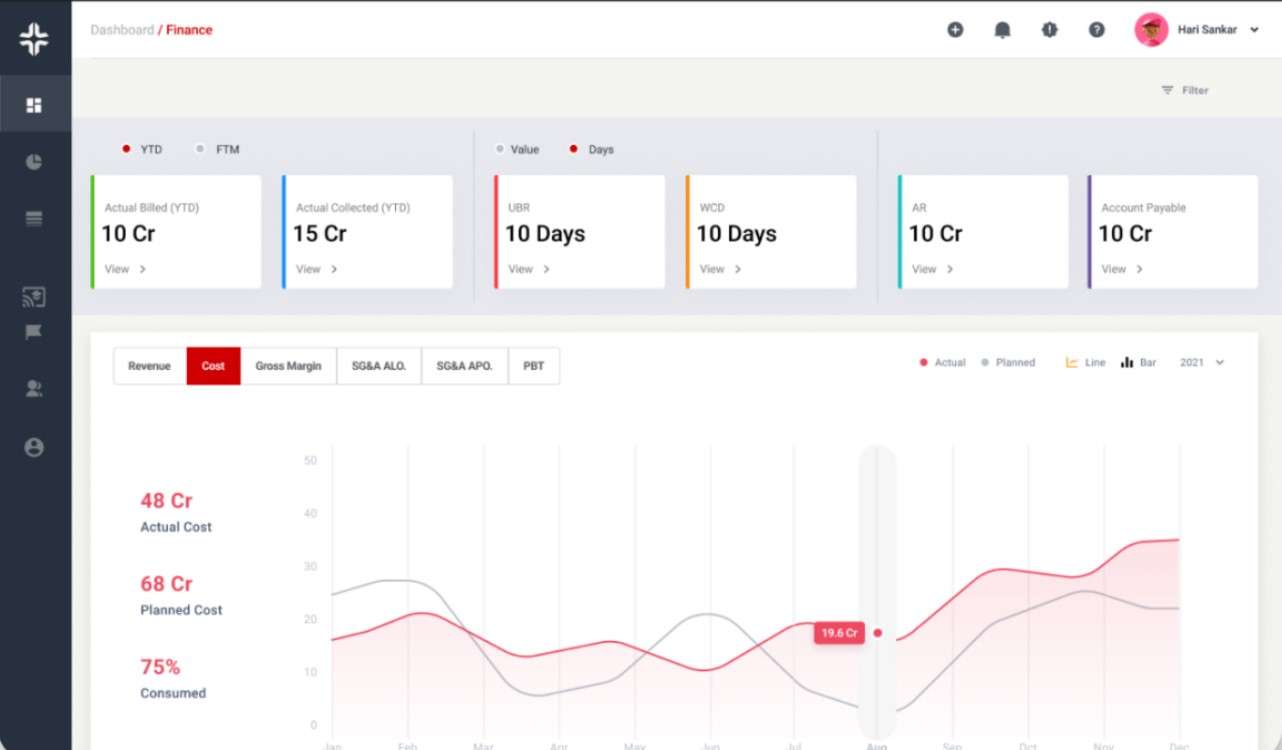
KEBS Reports & Analytics
Ready to optimize your Information Security Audit? Contact us today or request a demo to see KEBS in action!



